Physical IT Security Solutions
Maximize the security of laptops, desktops, and mobile devices anywhere with IT Pro Performance accessories

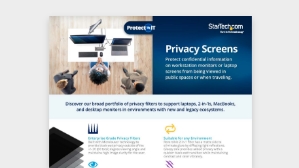
Protect Sensitive and Confidential On-screen Data
Privacy Screens
Prevent visual eavesdropping and improve data security with a privacy filter. Limit viewing angles on workstation monitors or laptop screens at the office or while traveling.

Featured Privacy Screen Products
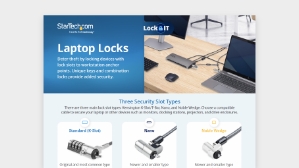
Prevent Hardware Theft
Laptop Locks • Anchors • Tethers
Discover the range of solutions available to secure your hardware and devices including universal 3-in-1 locks, tethers and anchors. Options available to support K-Slot/T-Bar, Nano Slot, and Noble Wedge lock slot devices.

IT Pro Tip:
Kensington style device lock slots have three main formats: K-Slot, Nano, and Noble Wedge. To learn how to choose a lock that is compatible with the slot on your specific device, check out the Laptop Locks Explained knowledge base article in our IT Pro Community.
Security Lock Featured Products
Safely and Securely Wipe Confidential Data From a Drive
Drive Erasers • Data Sanitization
Drive Erasers ensure confidential data belonging to an organization or employee is wiped from a drive (HDD or SSD). Data privacy and physical data security have become increasingly important for organizations, and stand-alone drive erasers can help the IT Pro efficiently and effectively clean confidential data from drives quickly and easily.

IT Pro Tip: Drive Erase Methods
Standalone drive erasers allow you to simply select your settings and go, no PC or additional software required.
No PC, and no additional software required. To learn more about the various levels of erasing available check out the Drive Erase Methods article on our IT Pro Community.
Drive Eraser Featured Products
Other Unique IT Pro Solutions
Racking • Charging • Mounting
Learn about other unique solutions to
secure your hardware and data.